Geofencing 101: A Beginners Guide…
August 20, 2015 - 3 minutes read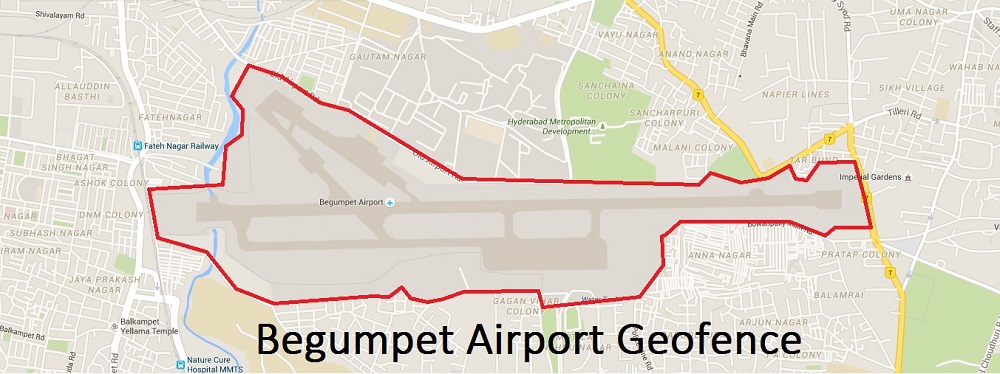
Services available through Zippr rely heavily on geofencing. When integrating with our partners we urge them to specify areas to which they can fulfill orders to the best of their abilities, effectively and efficiently resulting in reduced order rejection rates and better customer service to our users through on-time deliveries and fulfilled orders. These specific areas are called ‘trade zones’ and in this case when digitized are called ‘geofences’ or ‘geographical fences’. So what exactly are they?
A simple Wikipedia Search will probably give you the best definition of what one is.
“A geofence is a virtual perimeter ”
…for a real-world geographic area. They are generated dynamically – as in a radius around a point (long-lat coordinates) or as one which blankets a region in a predefined polygon. Programs that incorporate geo-fencing allow an administrator to set up triggers so when a ‘Location Aware Device’ enters (or exits) the boundaries defined by the administrator, a text message, email alert or a notification is sent.
Due to the utility of geofences, this technology is picking up pace rapidly. A few cases have been listed below.
1. Used with child location services, can notify parents if a child leaves a designated area.
2. Used with location-access based firearms can allow those firearms to discharge only in locations where their firing is permitted, thereby making them useless for crimes.
3.Geofencing is a critical element to telematics hardware and software. It allows users of the system to draw zones around places of work, customer’s sites and secure areas. These geofences when crossed by an autonomous/equipped vehicle or person, can trigger a warning to the user or operator via SMS or Email.
4.In some companies, geofencing is used by the Human Resource department to monitor employees working in special locations especially those doing field works. Using a geofencing tool, an employee is allowed to log his attendance using a GPS-enabled device when within a designated perimeter.
5.Other applications include sending an alert if a vehicle is stolen and notifying rangers when wildlife stray into farmland.
6. Geofencing, in a security strategy model, provides security to wireless local area networks. This is done by using predefined borders, e.g., an office space with borders established by positioning technology attached to a specially programmed server. The office space becomes an authorized location for designated users and wireless mobile devices.
7. Weaponized Drones and Hobby Radio Controlled Model Airplanes are sometimes fed geofence data to override the commands of their unsophisticated/unskilled operators, preventing the device from flying into protected airspace.
8. With an increasing popularity of mobile advertising , geofencing has been employed to distribute location-specific ads to customers on their mobile devices at airports, shopping malls etc.
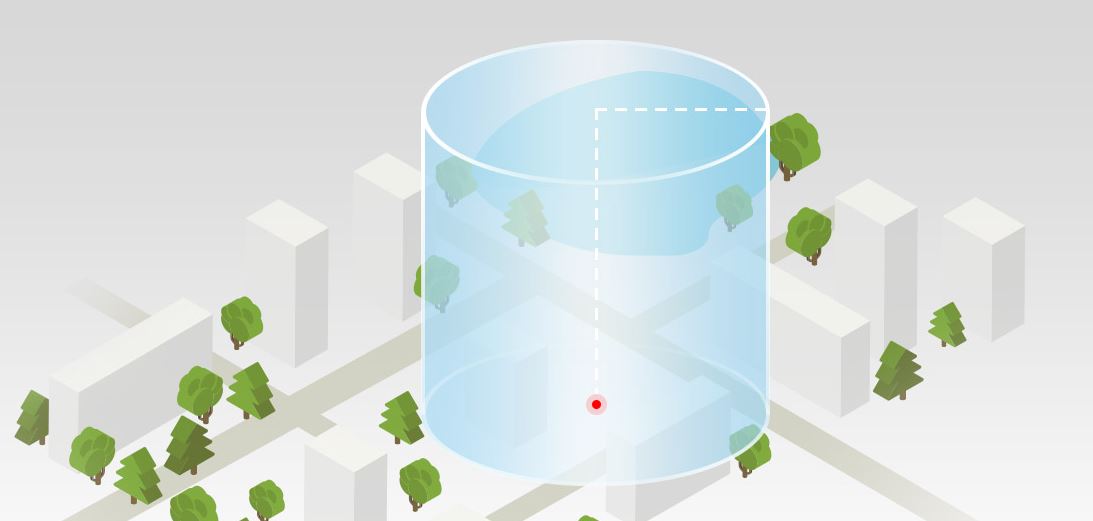
A 3-Dimensional Geofence used by DJI (drone company) in beginner training mode (Picture courtesy heliguy.com)
Interested in partnering with us? Contact partnerships@zippr.in